Protecting your small business data is non-negotiable. Cloud encryption ensures your sensitive information - like customer details, financial records, and AI logs - stays secure even if accessed without permission. Here are three key encryption techniques every small and midsize business (SMB) should know:
To make smart decisions about encryption, it’s crucial to understand how it actually works. Think of encryption keys as digital locks - they scramble your data into unreadable code and only the correct key can unlock it. But here’s the catch: if you lose those keys, you could permanently lose access to your data. And storing the keys alongside your encrypted files? That’s like hiding your house key under the doormat - an open invitation for trouble. Now, let’s break down how encryption applies to different states of cloud data.
Cloud data falls into three categories: data at rest, data in transit, and data in use. Data at rest includes stored files, databases, and backups. Most major cloud providers automatically encrypt this type of data using AES-256, a highly secure encryption standard approved by NIST. Data in transit - like information traveling over networks via HTTPS or API calls - is safeguarded with secure protocols like TLS. Meanwhile, data in use refers to information actively processed in memory, which is typically protected through application-level security and access controls.
Encryption methods also vary. Symmetric encryption uses a single secret key and is great for securing large volumes of data efficiently. On the other hand, asymmetric encryption relies on a public/private key pair. While it’s slower, it’s essential for securing web connections - like when you access a cloud-based CRM over HTTPS.
For AI-driven platforms like My AI Front Desk, encryption is a must at every level. Use AES-256 for stored data such as call recordings, transcripts, and lead details. For live data - like phone calls, texts, webhook notifications, and API interactions - TLS ensures secure communication. When evaluating cloud tools, whether it’s for file storage, a CRM, or an AI receptionist, verify that they encrypt both data at rest and in transit. Also, make sure encryption keys are stored separately from your business data to maximize security.
Lastly, remember the shared-responsibility model of the cloud. Providers handle infrastructure security and offer built-in encryption tools, but it’s up to you to enable these features, safeguard your keys, and control access to decrypted data. Start by ensuring your cloud storage, CRM, and communication platforms use AES-256 for stored data and TLS 1.2 (or higher) for connections. These baseline protections are essential for keeping your business data secure.
AES is a widely trusted encryption method used to secure stored files, databases, and backups by providers like AWS, Azure, and Google Cloud. This algorithm, approved by NIST, transforms data into ciphertext, ensuring that even if someone gains unauthorized access to your hard drive or cloud storage, the information remains unreadable without the decryption key. Let’s dive into how AES-256 is implemented by providers and what steps you should take to ensure its effectiveness.
Most cloud providers use AES-256 by default - the 256-bit key version considered the gold standard in the industry. It’s crucial to confirm that AES-256 encryption is active across all your cloud resources. Providers typically enable this encryption automatically for storage services, databases, and disk volumes. To stay secure, ensure encryption is enabled for all existing resources and set policies to automatically encrypt any new assets.
Key management is another critical piece of the puzzle. Use a dedicated key management service (KMS), such as AWS KMS or Azure Key Vault, to securely store and rotate AES keys separately from your data . Implement strict role-based access controls and maintain secure backups of your encryption keys to prevent unauthorized access.
The performance impact of using AES is minimal. Thanks to modern CPUs that accelerate AES processing, performance remains strong even for small-to-medium business workloads, such as CRM systems, file storage, or call recordings. Cloud providers design their storage systems to handle the encryption overhead efficiently, making AES a cost-effective security measure that won’t disrupt day-to-day operations.
Take, for instance, a 25-person professional services firm. They might store sensitive client documents, call transcriptions from an AI receptionist, and billing records in cloud storage and managed databases. By enabling default AES-256 encryption, using provider-managed KMS keys with automated rotation, and enforcing strict access controls, the firm can meet regulatory and contractual obligations. At the same time, this approach keeps IT management straightforward, even for a small team.
While AES encryption is excellent for securing data at rest, end-to-end encryption (E2EE) and client-side encryption take security a step further by protecting data throughout its entire lifecycle - from creation to sharing and storage. Here's the difference: AES focuses on stored data, while E2EE and client-side encryption ensure your data stays secure from the moment it's created until it's consumed. With E2EE, data is encrypted on the sender's device and only decrypted on the recipient's device, leaving no room for cloud providers or intermediaries to access the plaintext. Similarly, client-side encryption encrypts files before they leave your device and keeps them encrypted in the cloud until they're decrypted locally. This approach prevents anyone else from accessing your data, making it particularly useful for workflows involving highly sensitive information.
For small and medium-sized businesses (SMBs), this level of encryption is a game-changer for protecting critical communications and sensitive files. Whether you're dealing with legal documents, HR records, financial data, or customer information, these encryption methods can provide an added layer of security. For example, if you're using My AI Front Desk to handle customer calls and manage lead information, applying client-side encryption to call recordings, transcripts, and CRM exports ensures that only your business can decrypt and access these sensitive materials. This way, you can still leverage cloud-based automation and analytics without compromising confidentiality. As noted by Venn, end-to-end encryption and bring-your-own-key models "give organizations extra control in the cloud, providing assurance that only they can decrypt their data."
However, there is a trade-off: managing encryption keys. Unlike provider-managed encryption, you'll need to handle tasks like generating, storing, rotating, and backing up your encryption keys. Losing these keys can result in permanent data loss, so it's crucial to have well-documented procedures in place, especially for offboarding. Fortunately, many tools designed for SMBs now offer centralized key management systems with user-friendly interfaces to simplify this process.
Performance concerns are generally minimal for most SMB workloads, thanks to efficient algorithms like AES-256 and ChaCha20. That said, encrypted content can limit certain features, such as server-side search or full-text indexing, since providers can't read the data. A practical approach for SMBs is to apply E2EE selectively - encrypting only the most sensitive data while leaving lower-risk files accessible for collaboration and search.
To get started, focus on identifying your highest-risk workflows. These might include handling customer PII, payment information, health records, or legal documents. Once identified, choose tools that offer strong E2EE and client-side encryption options. Look for vendors that provide FIPS-validated cryptography, customer-managed key features, and clear documentation on key storage practices. Many mainstream platforms for cloud storage, email, and messaging now include built-in end-to-end encryption options that can be activated through simple admin interfaces. By pinpointing your critical workflows, you can determine where these advanced encryption techniques will provide the most protection.
Encryption is only as strong as its key management. Lose your keys or manage them poorly, and you could find yourself permanently locked out of your data.
For small and medium-sized businesses (SMBs) exploring cloud security, understanding the three primary approaches to managing encryption keys is essential. Each method has its own balance of security, complexity, and cost.
Let’s break down these approaches:
Provider-managed KMS is the easiest option to get started with. Services like AWS KMS, Azure Key Vault, and Google Cloud KMS handle the creation, storage, rotation, and auditing of encryption keys. These services integrate smoothly with other cloud tools, making them a convenient choice for SMBs.
The provider takes care of key backups, durability, and secure storage. All you need to do is configure access controls through a web interface. This simplicity makes provider-managed KMS a great fit for businesses without dedicated security teams. However, it’s worth noting that the cloud provider technically has access to your keys. A significant breach at their end could potentially expose both your encrypted data and the keys protecting it.
BYOK and CMK offer more control over your encryption keys. With BYOK, you generate your keys in your own environment - often using a hardware security module (HSM) - and then upload them to the cloud provider’s KMS. This ensures the provider only uses the keys you supply, giving you tighter control over their lifecycle.
This approach is particularly useful in regulated industries like healthcare, finance, or legal services. For instance, if you’re using My AI Front Desk to handle sensitive customer interactions in a medical setting, BYOK ensures only your business can authorize key changes. This added control supports compliance with strict regulations while still allowing you to leverage cloud-based automation.
The tradeoff? BYOK introduces more complexity. You’ll need to manage key rotation schedules, secure key material locally, and ensure rotation events don’t disrupt your applications.
Customer-held keys - sometimes referred to as "Hold Your Own Key" (HYOK) - take security to the highest level by keeping encryption keys entirely outside the cloud provider’s infrastructure. With this setup, your keys remain in your own HSM or a third-party key manager, and the cloud provider only receives temporary tokens for specific operations.
This approach ensures that even if the cloud provider experiences a major breach, your master keys remain safe. However, this level of separation comes with significant challenges. You’ll need to build and maintain dedicated key infrastructure, ensure high availability, monitor the system, and integrate it with your cloud workloads. For most SMBs, this option is too resource-intensive without specialized expertise or support from a managed service partner.
| Approach | Who Creates Keys? | Data Protection Level | Implementation Difficulty | Best For |
|---|---|---|---|---|
| Provider-Managed KMS | Cloud provider | Strong, though provider has access | Low – quick to enable | General business data, limited IT staff |
| BYOK / CMK | Customer (imported to KMS) | Stronger; provider uses but doesn’t create keys | Medium – requires key lifecycle planning | Regulated data, compliance requirements |
| Customer-Held Keys | Customer only (kept outside cloud) | Highest; provider cannot decrypt | High – needs HSM and integration work | Scenarios demanding strict data sovereignty |
To decide which method suits your needs, start by classifying your data:
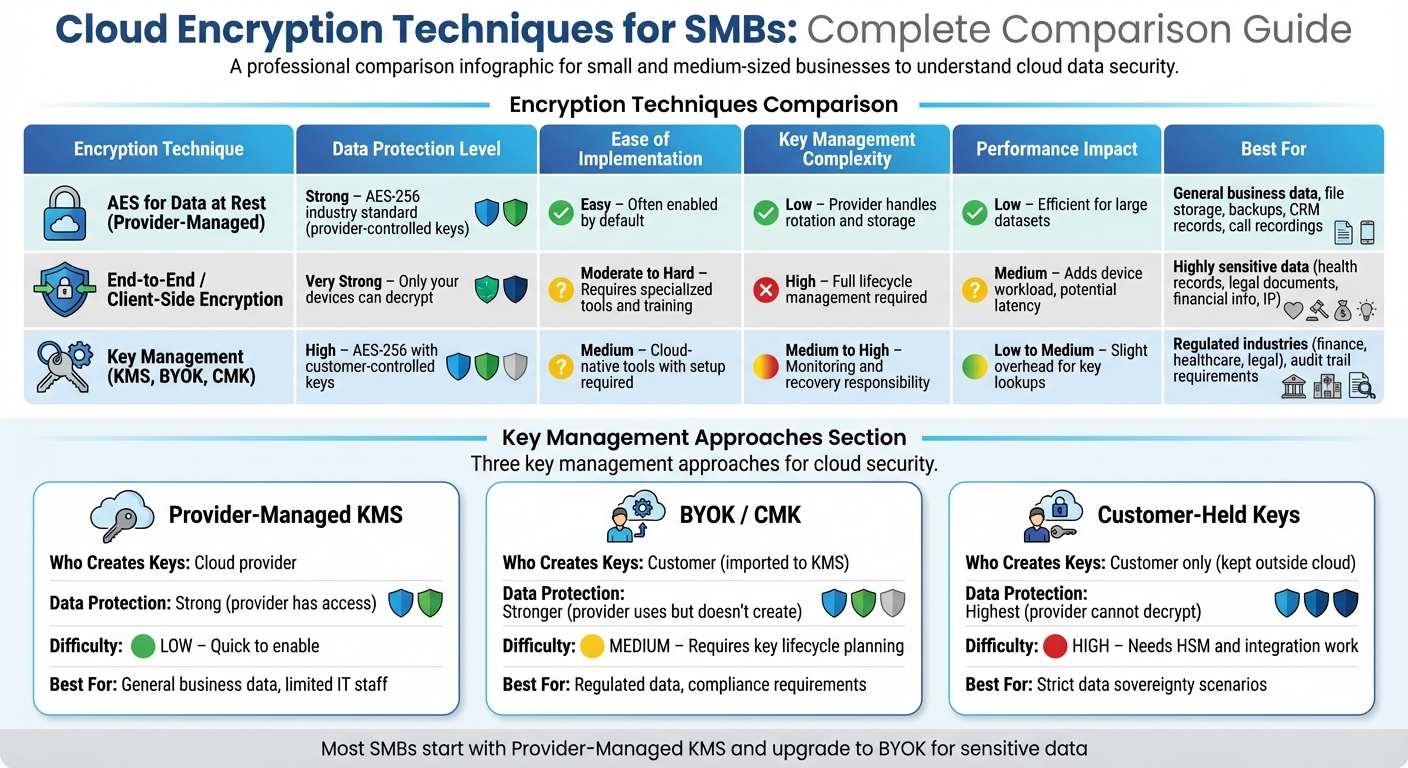
Cloud Encryption Techniques Comparison for Small Businesses
This table breaks down encryption techniques tailored for SMBs, focusing on protection levels, ease of use, key management, performance, and ideal applications.
| Encryption Technique | Data Protection Level | Ease of Implementation | Key Management Complexity | Performance Impact | Best For |
|---|---|---|---|---|---|
| AES for Data at Rest (Provider-Managed) | Strong – AES-256 is the industry standard, though keys are typically controlled by the cloud provider | Easy – Often enabled by default; just a checkbox in most cloud management dashboards | Low – The provider handles key rotation and storage, leaving you to manage access permissions | Low – Symmetric AES is efficient, even for large datasets | General business data, file storage, backups, CRM records, and call recordings when regulations are minimal |
| End-to-End / Client-Side Encryption | Very Strong – Only your devices can decrypt, ensuring providers cannot access plaintext data | Moderate to Hard – Requires specialized tools, application changes, and user training | High – You manage the full key lifecycle, including generation, storage, sharing, and recovery | Medium – Adds workload on devices, potentially causing latency on low-power hardware | Handling highly sensitive data (e.g., health records, legal documents, financial info, intellectual property) where strict compliance is required |
| Key Management (KMS, BYOK, CMK) | High – AES-256 encryption with customer-controlled keys using KMS or external HSM | Medium – Relies on cloud-native tools but requires setup for policies and key rotation | Medium to High – KMS simplifies key handling, but you’re responsible for monitoring and recovery | Low to Medium – Slight overhead for key lookups, usually negligible for SMB workloads | Regulated industries (finance, healthcare, legal) and SMBs needing audit trails and demonstrable key control |
For many U.S. SMBs, provider-managed AES encryption strikes the right balance between security and simplicity. Services like AWS, Azure, and Google Cloud integrate this type of encryption seamlessly, making it an excellent choice for safeguarding routine data like call recordings, CRM records, and file storage without requiring additional configuration.
However, when dealing with sensitive data - such as PHI, payment details, or legal files - end-to-end encryption or customer-managed keys (BYOK) become critical. These methods ensure you maintain exclusive control over decryption, meeting stricter compliance standards like HIPAA, PCI-DSS, and state privacy laws. The tradeoff? Increased complexity, as you’ll need robust processes for key backup and recovery.
This comparison highlights the importance of tailoring encryption strategies to your specific security needs, balancing ease of use with the level of control required.
For small businesses in the U.S., encryption doesn’t have to be overwhelming or expensive. A multi-layered approach can provide effective protection. Start with AES-256 encryption for data at rest, which secures your stored files, databases, and backups by making unauthorized access virtually useless. The good news? Most major cloud platforms already include this level of protection as a standard feature.
When dealing with sensitive data - like customer payment information, health records, legal documents, or detailed call transcripts from tools such as My AI Front Desk - end-to-end encryption or client-side encryption offers an additional layer of security. These methods ensure that only authorized devices and users can decrypt the data, making it easier to meet compliance requirements like HIPAA or various state privacy laws.
One critical component of encryption is key management. Using tools like a cloud Key Management Service (KMS), Bring Your Own Key (BYOK), or customer-managed keys gives you better control over access, reduces the risk of insider threats, and creates audit trails to help with regulatory compliance. However, even the strongest encryption can fail without disciplined key handling. This includes setting clear access policies, regularly rotating keys, and maintaining secure backups.
Together, these measures form a practical "defense in depth" strategy. Even if an attacker gains access to a storage bucket, intercepts traffic, or exploits a misconfigured account, they would still need the encryption keys to access meaningful data. This layered approach significantly reduces the impact of common security incidents like stolen devices, phishing attacks, or configuration errors.
To get started, ensure that AES encryption is enabled on all your cloud services. Identify your most vulnerable workflows and apply end-to-end encryption or customer-managed keys where they’re needed most. Document key ownership, establish secure backup systems, and create contingency plans for staff transitions or system failures. These straightforward steps turn basic encryption into a powerful tool for protecting your business’s revenue, reputation, and customer trust. By taking these precautions, you’ll be better equipped to safeguard both your operations and the confidence of your customers.
AES encryption relies on a symmetric key, meaning the same key is used to both encrypt and decrypt data. This method is known for its speed and efficiency, but it comes with a crucial requirement: the encryption key must be managed securely to prevent unauthorized access.
With end-to-end encryption (E2EE), data is encrypted on the sender's device and remains encrypted until it reaches the recipient's device, where it is finally decrypted. This approach ensures that no intermediaries - such as servers or service providers - can access the data at any point.
Client-side encryption takes privacy a step further by encrypting data directly on the user’s device before it’s sent to a server or cloud storage. Similarly, decryption happens on the user’s device, giving users complete control over their data and ensuring maximum privacy and security.
To keep encryption keys secure and minimize the risk of data loss, small and medium-sized businesses (SMBs) should consider these practical steps:
These measures can help SMBs strengthen their data security and safeguard sensitive information effectively.
Businesses might consider using customer-managed encryption keys when they require complete control over their encryption process. This ensures that only the business has access to the encryption keys, offering an added layer of security.
This approach is particularly suited for organizations dealing with highly sensitive information, adhering to strict compliance standards, or aiming to block unauthorized access by third parties. Industries such as healthcare, finance, and legal services - where safeguarding data is paramount - can especially benefit from managing their own encryption keys, as it strengthens privacy and security measures.
Start your free trial for My AI Front Desk today, it takes minutes to setup!








