Key Lifecycle Management (KLM) is the process of securing cryptographic keys throughout their entire lifecycle - from creation to destruction. Managing these keys effectively is critical for protecting encrypted data, maintaining compliance with regulations like GDPR and HIPAA, and safeguarding against breaches. The six stages of KLM are:
Poor key management can lead to security failures, as seen in the 2011 RSA breach. To prevent this, organizations should implement clear policies, centralized systems, and automation tools for tasks like key rotation and certificate renewal. For example, using cloud-based KMS or HSMs enhances security while reducing manual effort. Automation is increasingly essential as certificate lifespans shorten, dropping to just 47 days by 2029.
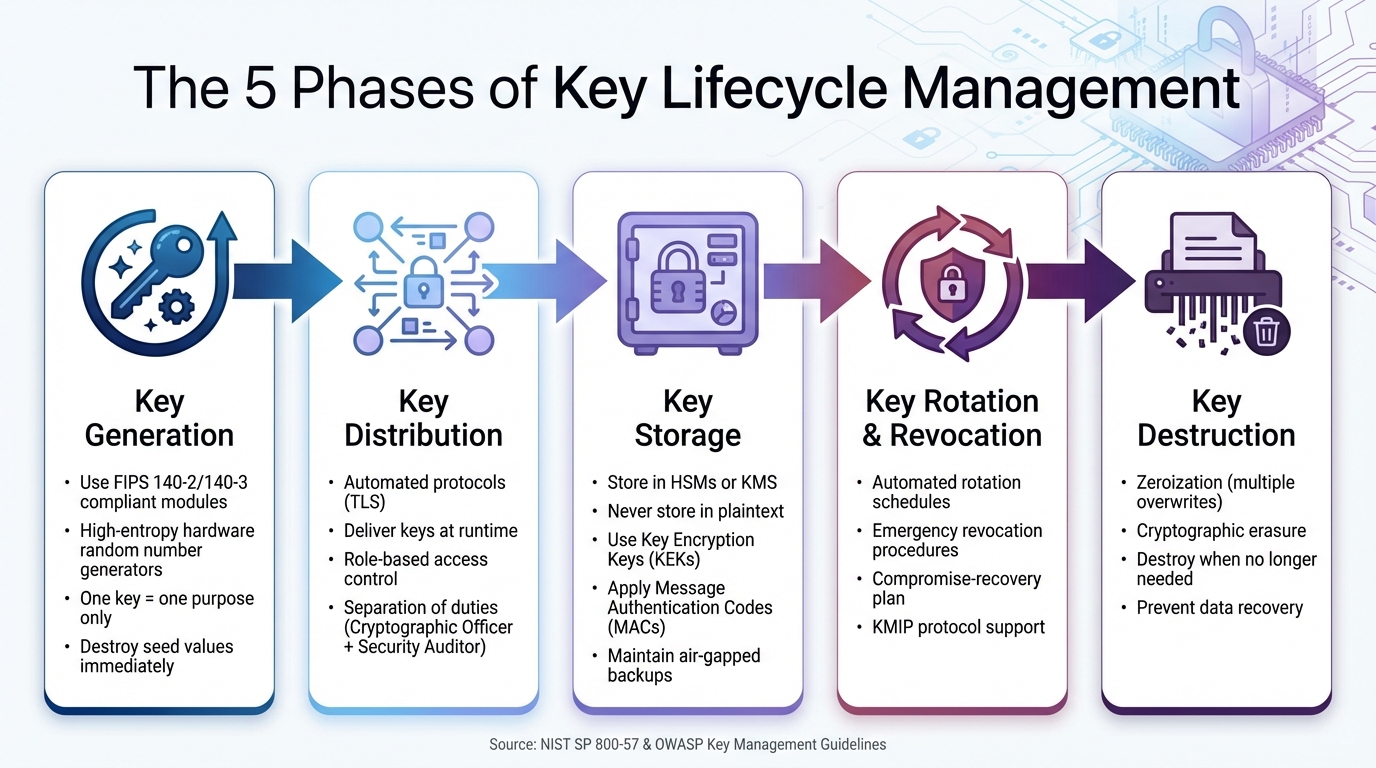
5 Phases of Key Lifecycle Management Process
Grasping the five essential phases of key lifecycle management is crucial for setting up a strong security framework. These phases cover the journey of a key, from its creation to its eventual retirement. Let’s break down each phase in detail.
The foundation of secure key management begins with unpredictable key creation. This process relies on FIPS 140-2 or 140-3 compliant cryptographic modules that use high-entropy hardware random number generators (HRNGs) to produce truly random values. This randomness is critical for ensuring the strength of keys.
To guard against evolving threats, keys must have strong lengths. Once a key is generated, any seed values or unnecessary copies should be destroyed immediately to prevent unauthorized reconstruction.
"A single key should be used for only one purpose (e.g., encryption, authentication, key wrapping, random number generation, or digital signatures)." - NIST SP 800-57
This principle of key separation ensures that if one key is compromised, the damage is contained. It also prevents cryptographic processes from interfering with each other. After secure key creation, the next step is ensuring safe distribution.
Sharing keys securely is a critical step that relies on automated protocols instead of manual transfers. Encrypted channels, such as TLS, should be used to transport keys securely. Keys should be delivered at runtime rather than embedded in source code.
Enforcing strict access controls during this phase is essential. Assign specific roles, such as a "Cryptographic Officer" for key generation and recovery, and a "Security Auditor" for oversight. This separation of duties ensures no single person has unchecked control over the key lifecycle. With secure distribution in place, the focus shifts to proper key storage.
Keys must be stored in Hardware Security Modules (HSMs) or Key Management Systems (KMS) that provide tamper-resistant protections. These systems ensure that keys are shielded from unauthorized access. Keys should never exist in plaintext; instead, software-based keys at rest must be encrypted using Key Encryption Keys (KEKs) that match or exceed the original key's cryptographic strength.
To detect unauthorized modifications, apply Message Authentication Codes (MACs) to stored keys. Additionally, maintain air-gapped backups of critical keys in offline storage for disaster recovery scenarios. Separating keys based on their purpose - such as storing CA infrastructure keys separately from customer data encryption keys - reduces the potential impact of a breach. Secure storage sets the stage for effective key rotation and revocation.
Regular automated key rotation minimizes the risk associated with key compromise by limiting the amount of data protected by a single key. Many Cloud Key Management Services and KMS platforms handle this process automatically, ensuring continuous security monitoring.
In the event of a compromise, emergency revocation procedures must be ready. These procedures should be part of a compromise-recovery plan that includes contact information, re-key methods, and an inventory of all certificates. The Key Management Interoperability Protocol (KMIP) enables systems to communicate and automate revocation processes across platforms. Once keys are rotated or revoked, secure destruction is the final step.
When keys are no longer needed, secure destruction ensures they cannot be recovered or misused. Techniques like zeroization, which overwrites key material multiple times, or cryptographic erasure, which deletes the wrapping key protecting the stored key, are effective.
Keys should be destroyed as soon as they are no longer required for operational or legal purposes. This includes keys that have reached the end of their cryptoperiod, been replaced through rotation, or been compromised. Proper destruction ensures that even if attackers gain access to old storage systems, they cannot retrieve historical data.
Turning lifecycle protocols into actionable steps ensures strong protection. Even small businesses and agencies with limited budgets and teams can implement practical measures like clear policies, centralized control, and consistent oversight to minimize risks. These practices not only strengthen security but also serve as a foundation for choosing effective management tools, which we'll explore in later sections.
Every organization should have a well-defined Key Management Policy (KMP) and Practice Statement (KMPS) that outline how keys are protected. These documents should clearly state who has access to keys, how they are used, and what steps to follow if an issue arises.
A key defense is separating roles to prevent any one person from compromising the system. For instance, you might designate a Cryptographic Officer to handle tasks like key generation, backup, and recovery, while a Security Auditor ensures compliance.
"Accountability involves the identification of those that have access to, or control of, cryptographic keys throughout their lifecycles." - OWASP
To protect keys further, implement role-based access control (RBAC) so that only authorized personnel can access them. Each key should be assigned a single purpose, such as encryption or digital signatures. Keeping an up-to-date inventory of keys - complete with metadata like creation dates, approved algorithms, and ownership - ensures better oversight.
Centralized Key Management Systems (KMS) streamline processes like key generation, distribution, rotation, and destruction. By automating these tasks, you reduce manual effort and the likelihood of human error. A centralized KMS provides a single control point, ensuring consistent enforcement of policies, RBAC, and improved visibility into key inventories, which helps meet regulatory requirements.
"Robust key management ensures keys remain confidential, available when needed, and cryptographically strong." - SSL.com
Standards like the Key Management Interoperability Protocol (KMIP) make it easier to manage keys across different platforms. Automated features like periodic key rotation and encrypted backups stored in air-gapped or offline environments help limit data exposure and ensure recovery in case of catastrophic loss.
Regular audits are crucial - not just for compliance, but for identifying and addressing potential issues before they become serious. Metadata for each key, such as creation dates, approved algorithms, and ownership, should be carefully documented. Monitoring access attempts and usage patterns can help detect unusual activity.
Automated alerts for key expirations, revocations, or configuration errors can prevent disruptions. Organizing keys by business unit or priority and assigning dedicated teams to handle audit findings adds another layer of protection. For hardware-based systems like Hardware Security Modules (HSMs), it’s vital to monitor for tamper events, such as unauthorized physical access or configuration changes.
"Highly unusual events should be noted and reviewed as possible indicators of attempted attacks on the system." - OWASP
To stay aligned with your Key Management Policy, security plans and procedures should be audited at least once a year. Regular network scans can confirm that deployed certificates match the central inventory. With certificate lifespans shortening, automated monitoring and renewal have become indispensable.
These practices lay a solid foundation for choosing tools that will automate and secure your key management processes effectively.
After setting up strong policies and centralized controls, the next step is finding tools that can automate and secure your key operations. The right tools not only enhance security but also streamline operations, making them more efficient. Your choice will depend on your security requirements and budget.
Hardware Security Modules (HSMs) are specialized devices designed to keep cryptographic keys safe. These tamper-resistant tools generate and store keys in isolated hardware environments, ensuring that even if your network is compromised, the keys remain secure. HSMs use secure boot mechanisms and physical protections to maintain the integrity of key operations.
However, HSMs come with higher upfront costs and require specialized handling, making them a better fit for organizations with strict security requirements. Industries like finance, healthcare, and government contracting often rely on HSMs to meet regulatory standards and protect sensitive data.
For instance, past cybersecurity breaches have underscored the importance of robust hardware protection, highlighting the risks of relying on less secure alternatives.
For smaller businesses, cloud-based Key Management Services (KMS) such as AWS KMS or Azure Key Vault offer a simpler, more affordable solution. These platforms handle key generation, storage, and rotation without the need for physical hardware or advanced technical expertise. They operate on a pay-as-you-go model, charging based on how many keys you store and how often you use them.
Cloud KMS platforms are designed to integrate seamlessly with cloud infrastructure and SaaS applications, making them a great option for businesses already operating in the cloud. While they lack the physical tamper-resistance of HSMs, they provide robust security for most use cases at a much lower cost.
| Feature | Hardware Security Modules (HSMs) | Cloud Key Management Services |
|---|---|---|
| Security | Physical tamper-resistance; isolated hardware key generation | Logical isolation with RBAC; encrypted cloud storage |
| Scalability | Limited by hardware capacity | Highly scalable, with cloud-native automation |
| Cost | High initial investment and maintenance | Low overhead; usage-based pricing |
| Management | Requires expert handling | Fully managed by the provider |
Whether you choose hardware or cloud solutions, automation has become essential for managing key operations. As certificate lifetimes continue to shrink - dropping from one year to 200 days in March 2026, then to 100 days in 2027, and finally to just 47 days by 2029 - manual management is becoming impractical.
"Unless certificate renewal is automated, these changes are going to increase the direct operational costs related to the renewals as well as increase the likelihood of outages." – Red Sift
The Automated Certificate Management Environment (ACME) protocol simplifies this process by allowing servers to automatically obtain and renew certificates from Certification Authorities without human involvement. Small businesses should look for tools that support ACME, as it avoids vendor lock-in and works with free Certification Authorities like Let's Encrypt. Automation also takes care of tasks like key rotation, monitoring Certificate Transparency logs for unauthorized issuances, and emergency revocation across multi-cloud environments.
For businesses leveraging AI-driven platforms, secure and automated key management is critical. Tools like My AI Front Desk (https://myaifrontdesk.com), which manage sensitive customer interactions through AI receptionists, rely on automated key rotation and monitoring to secure encrypted communications and CRM integrations. This ensures confidentiality and system availability without requiring constant manual oversight.
Automation also plays a vital role in reducing noise in monitoring logs for businesses using AI-powered tools. By distinguishing routine activity from potential threats, automated systems help reduce alert fatigue, enabling teams to focus on real security issues.
Having a clear plan is crucial when rolling out a key management system. The approach you take will depend on factors like your organization's size, compliance needs, and existing infrastructure. A well-structured roadmap helps you steer clear of costly errors and ensures your system functions effectively when it matters most.
Your planning should align with the key lifecycle stages discussed earlier. Start by identifying the assets you need to secure and the specific goals you want to achieve. Consider whether you need to protect data at rest, in transit, or both. Define your objectives around confidentiality, authenticity, integrity, and non-repudiation. Compliance requirements - whether PCI DSS, GDPR, HIPAA, or NIST standards - will guide the minimum standards for key strength and storage methods.
Take stock of your threat landscape and how long your data needs protection. For high-security scenarios, the industry has moved from 2048-bit RSA keys to 3072-bit RSA, offering better protection against emerging threats. If your organization handles sensitive data like government contracts or financial records, consider quantum readiness. The Commercial National Security Algorithm Suite 2.0 can help ensure resilience against future quantum computing risks.
Assign clear roles for tasks like key generation, backups, and compliance oversight. Separating these duties reduces the risk of any one individual having too much control. Decide whether centralized or decentralized management suits your infrastructure better, and evaluate whether hardware security modules (HSMs) or cloud-based solutions align with your budget and technical needs.
| Assessment Factor | Key Considerations |
|---|---|
| Security Services | Confidentiality, Integrity, Authenticity, Non-repudiation |
| Key Types | Symmetric, Asymmetric, HMAC, Key Encryption Keys (KEKs) |
| Storage Requirements | Volatile vs. persistent memory, HSM vs. software vault |
| Lifecycle Phases | Generation, Distribution, Storage, Rotation, Revocation, Destruction |
| Compliance | PCI DSS, GDPR, HIPAA, NIST SP 800-57 |
Once you've nailed down these requirements, you can focus on avoiding common mistakes in key management.
The 2011 RSA breach serves as a stark reminder of the importance of strict key segmentation and automated protocols.
Avoid manual key transfers or embedding keys directly into applications. Instead, rely on automated, secure protocols like TLS for key delivery. Use cryptographic segmentation to separate keys by purpose - for example, keeping Certificate Authority (CA) keys separate from those used for encrypting customer data. This minimizes the damage in case of a breach.
Adopt "sealed vault" operations, where all cryptographic activities (encryption, decryption, signing) occur within secure environments like HSMs. Plaintext keys should never interact with standard application code. Also, establish a formal compromise-recovery plan. This should include contact details for key personnel, re-keying methods, and a complete inventory of keys to act on immediately if a breach occurs.
"Data that has been encrypted with lost cryptographic keys will never be recovered. Therefore, it is essential that the application incorporate a secure key backup capability." – OWASP
By sidestepping these mistakes, you’ll be better prepared to implement a functional deployment plan.
Base your implementation on the best practices outlined above. Begin with a proof of concept before committing to a full deployment. Test your Key Management System (KMS) or Certificate Lifecycle Management tool to ensure it integrates seamlessly with your existing platforms and software. Use certificate transparency logs to keep track of all domains and assign clear ownership within your team.
For network monitoring, opt for agentless scanning to identify certificate deployments without the hassle of installing agents. Organize your Public Key Infrastructure (PKI) into groups based on business units to ensure alerts reach the right people. Implement Certificate Authority Authorization (CAA) policies to block unauthorized certificate issuance from inactive DNS records. If your business uses AI-driven platforms like My AI Front Desk (https://myaifrontdesk.com), automated key rotation and monitoring are critical for securing encrypted communications and simplifying CRM integrations.
Maintain an up-to-date key inventory, including metadata like creation dates, algorithms, usage, and ownership. Regularly monitor this metadata and keep track of expiration dates. With certificate lifetimes shrinking - 200 days by March 2026, 100 days by March 2027, and just 47 days by March 2029 - automation will be essential to keep up.
"A single key should be used for only one purpose (e.g., encryption, authentication, key wrapping, random number generation, or digital signatures)." – NIST
Cryptographic keys are the backbone of data security. Without proper lifecycle management, even the strongest encryption can fall short. Managing these keys effectively is not just a technical necessity - it’s also critical for meeting compliance requirements for standards like PCI DSS, GDPR, HIPAA, and NIST. Poor key management can lead to serious security vulnerabilities, unexpected outages from expired certificates, and an inability to keep up with emerging threats.
The industry’s move toward shorter certificate lifespans highlights the growing importance of automation. Relying on manual processes is no longer practical. Organizations that delay adopting centralized Key Management Systems (KMS) or Certificate Lifecycle Management (CLM) tools risk being left behind as these changes accelerate.
"Failure to securely manage cryptographic keys may lead to security breaches and data loss." - Cloud Security Alliance
To strengthen key management, it’s important to go beyond basic practices and take proactive steps during implementation. Automation plays a major role here. Using ACME protocols can eliminate manual renewal tasks, while generating keys within FIPS-compliant Hardware Security Modules (HSMs) enhances security. Additionally, enforcing clear accountability and separation of duties helps reduce internal risks. For businesses leveraging AI-driven platforms like My AI Front Desk (https://myaifrontdesk.com), automated key rotation and monitoring ensure encrypted communications remain secure across multiple channels.
Having a documented recovery plan and a complete key inventory is essential for responding quickly to breaches. By centralizing oversight, automating routine tasks, and preparing for post-quantum migration, organizations can turn key lifecycle management into more than just a compliance checkbox - it becomes a strategic tool to protect both their data and their reputation.
Hardware Security Modules (HSMs) are specialized physical devices built to handle secure key management. They allow complete control over key generation, storage, and cryptographic tasks, all within a tamper-resistant setup. These devices are typically single-tenant, meaning they're dedicated to one user and not shared with others.
On the other hand, Cloud Key Management Services (KMS) are cloud-based, fully managed solutions. They simplify the process by abstracting the hardware layer, prevent key export for enhanced security, and include features like automatic key rotation and policy-driven access controls. Unlike HSMs, KMS solutions are multi-tenant, meaning they serve multiple users, but they are designed with strict security measures to ensure each user's data remains isolated and secure.
Automation plays a crucial role in Key Lifecycle Management, especially with certificate lifespans now as short as 47 days. Handling thousands of certificates manually in such a tight timeframe isn't just challenging - it’s a recipe for mistakes, missed renewals, and potentially expensive service outages. Automated tools take the stress out of this process by ensuring certificates are renewed and deployed on schedule with minimal hassle.
Beyond preventing outages, automation brings other benefits to the table. It minimizes human error, lowers operational costs, and frees up IT teams to tackle more strategic tasks. Plus, it offers real-time visibility into certificate inventories, making it easier to adapt to changes and scale as businesses expand. In today’s fast-moving digital landscape, automated lifecycle management isn’t just helpful - it’s essential for keeping systems secure and running smoothly.
Key lifecycle management (KLM) is all about handling cryptographic keys responsibly - from their creation to their eventual destruction. It’s a critical process for securing data and staying compliant with standards like PCI-DSS or GDPR. For small businesses with tight budgets, simplifying KLM can make it both practical and cost-effective.
Start by drafting a straightforward policy. This should clearly define who is responsible for managing keys, how long keys remain valid, and the steps for rotation and destruction. Automation can make this process much easier. Tools like cloud-based key management services (many of which have free tiers) can handle tasks like key rotation seamlessly. Using a centralized repository for storing keys also reduces the risk of errors and improves security oversight.
To keep expenses in check, explore open-source tools or free versions of commercial solutions. Maintain an up-to-date inventory of your cryptographic keys and schedule regular reviews to ensure they’re rotated or expired as needed. You can also set up automated audits using simple scripts or affordable monitoring tools. These small steps can help small businesses protect sensitive data effectively - without the need for a dedicated IT team.
Start your free trial for My AI Front Desk today, it takes minutes to setup!








